If you were once running all services on macOS Server then it may be that you are still using Open Directory. Open Directory is an LDAP/Kerberos service implementation and should work with a variety of UNIX and Linux systems. The following gives an example of enabling user login to a Linux client machine connected to Apple Open Directory. I have tested this procedure on Debian GNU/Linux 10, 11, and Ubuntu 20.04 LTS.
Password Server (Kerberos)
The simplest way to start is by setting up Kerberos only; we’ll add the user account information from LDAP latter. Enter all commands logged in as root, or precede all commands with ‘sudo’
apt install krb5-config krb5-user- You’ll be prompted for the Default Kerberos version 5 realm: which is likely your Open Directory servers domain name capitalised for example ‘PROFILEMANAGER.MACINTOSH-RESCUE.NET’
- Kerberos servers for your realm: will probably be the same in lowercase like ‘profilemanager.macintosh-rescue.net’
- Administrative server for your Kerberos realm: will likely be the same if you just have one server ‘profilemanager.macintosh-rescue.net’
- Now we can test the configuration by trying to acquire a Kerberos token with a known username:
kinit -P merlin - Enter the password when prompted then verify that the token has been acquired with:
klist
Getting Usernames & Group Info from Open Directory
We now need to setup access to the user information stored in Open Directory’s LDAP database then configure the system to allow login of a network user:
apt install libpam-krb5apt install libnss-ldap- LDAP server URI: should be something like ldap://profilamanager.macintosh-rescue.net
- LDAP server search base: should be made up from the servers domain name levels so mine is: ‘dc=profilemanager,dc=macintosh-rescue,dc=net’
- LDAP version to use: is 3
- Clear all the following dialogues and enter with their fields blank
- Allow LDAP admin account to behave like local root? : probably not.
- Does the LDAP database require login? : no
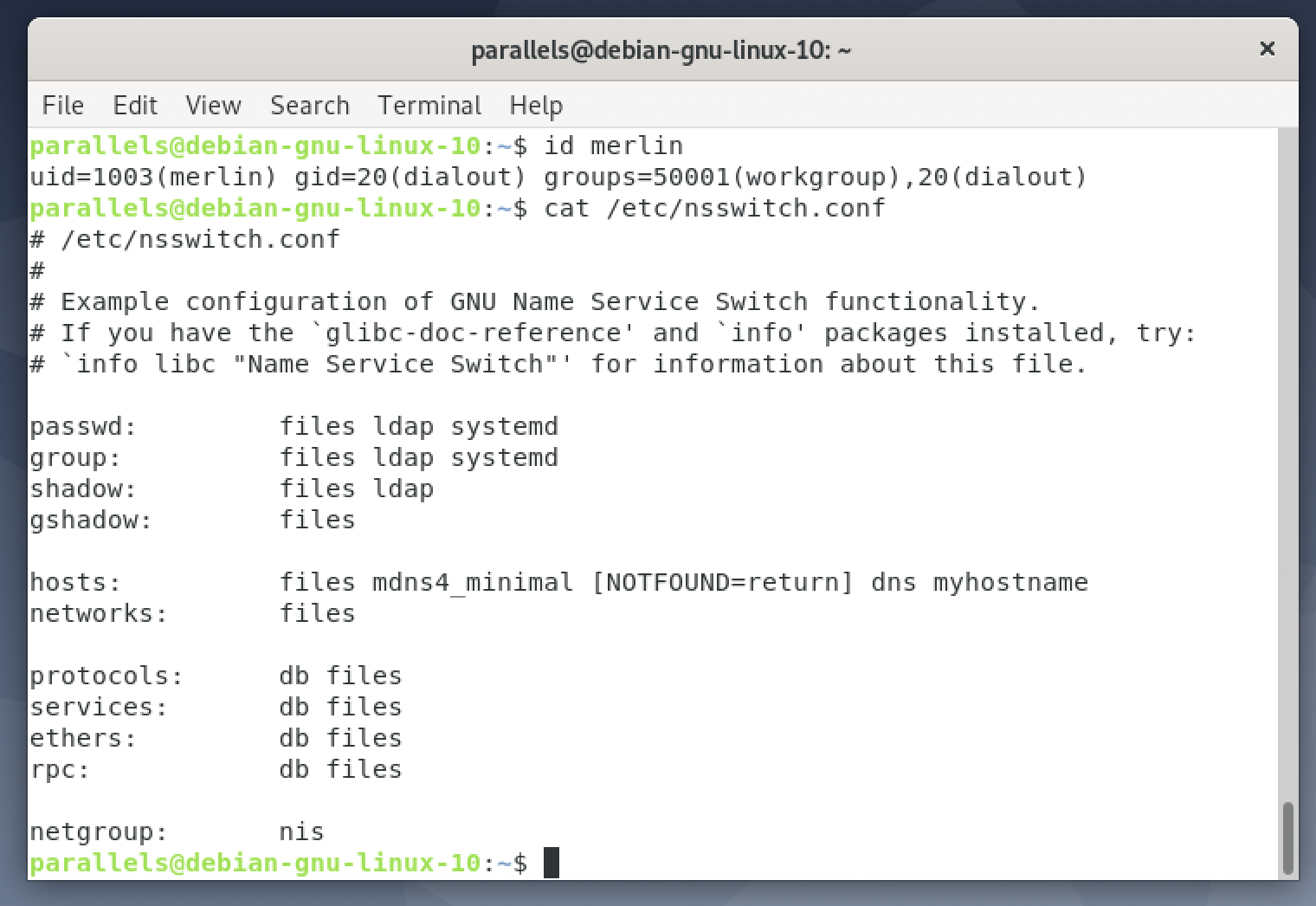
- Now edit the /etc/nsswitch.conf file and add ‘ldap’ to the entries for ‘passwd:’, ‘group:’ and ‘shadow:’ like this:

- The system should now be able to see Network Users so you can try something like:
id merlin#and see if you get some info. - I’d recommend rebooting the system and trying a text login for a network user; you should get to a shell but without a home directory so that’s the next thing to fix.
Automatic Home Directory Creation:
For users to be able to practically login to the system and work they need a home directory, although this may not be necessary if they are only accessing services.
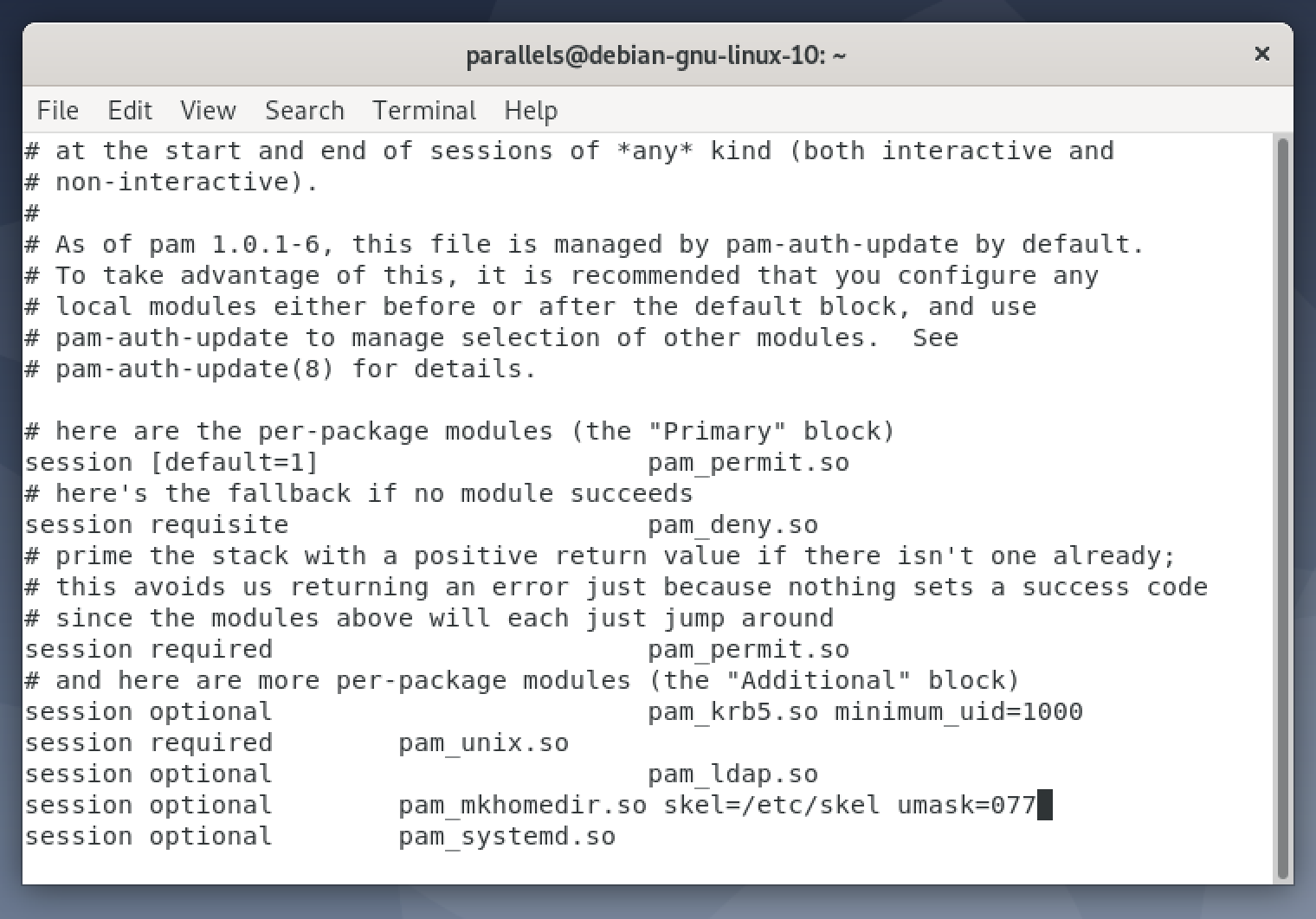
apt install oddjob-mkhomedirvi /etc/pam.d/common-session- Add the following line between ‘pam_ldap.so’ and ‘pam_systemd.so’: session optional pam_mkhomedir.so skel=/etc/skel umask=077

- Save the file, reboot and you should now be able to login as a Network User. Your home directory location is specified on the macOS Open Directory server so you will probably end up with a home directory stored in ‘/Users’ and not the ‘/home’ you’d expect on a linux system.
Conclusion
You should now be able to integrate a Debian based Linux system into an Apple centric directory service. Users can login, get a locally stored home folder in ‘/Users’, and they can administer their own passwords.
It will not be possible for the root user to change Open Directory passwords which would be true of a macOS client also.
Enjoy playing with your linux systems with integration into your network of Mac’s!